These types of attacks use social engineering to exploit human nature and often appeal to more salacious interests, says GreatHorn.

Image: iStock/OrnRin
Phishing emails try to entrap people by pushing subjects designed to exploit their fears, interests, anxieties and curiosity. Sometimes those subjects are of a professional or business nature. And other times they're of more personal or even prurient nature considered NSFW (not safe for work). In a new report published Wednesday, security provider GreatHorn looks at a couple of X-rated phishing campaigns that try to lure in certain people in an effort to blackmail them.
SEE: Social engineering: A cheat sheet for business professionals (free PDF) (TechRepublic)
For its latest research, GreatHorn discovered that phishing attacks are increasingly using X-rated material in emails aimed at corporate employees. Between May 2020 and April 2021, the number of such attacks jumped by 974%. The emails are typically sent to people with male-sounding names based on their email addresses.
But the attackers are actually using the initial phishing emails as a prelude to blackmail. In the first phase of the campaign, the user is encouraged to click on an email link that promises sexual material or interactions. Clicking the link automatically sends their email address to the linked site. Using this technique of email pass-through, the cybercriminals are setting up their victims for blackmail.
In the second phase, the attacker uses the email address and any other information obtained to target susceptible individuals. The follow-up email threatens to extort any user who clicked on the links in the first email and accessed potentially compromising material.
In its report, GreatHorn highlighted two different campaigns.
In the first one, the email claims to be from a woman who wants to meet you, either at your place or hers. Clicking the link in the message takes you to a site with photos, which directs you to what looks like a dating site. But this second site appears to be geared to trick people into providing payment information. Any data collected here is sent to the criminals who likely will use it for money withdrawal, blackmail or further fraud.
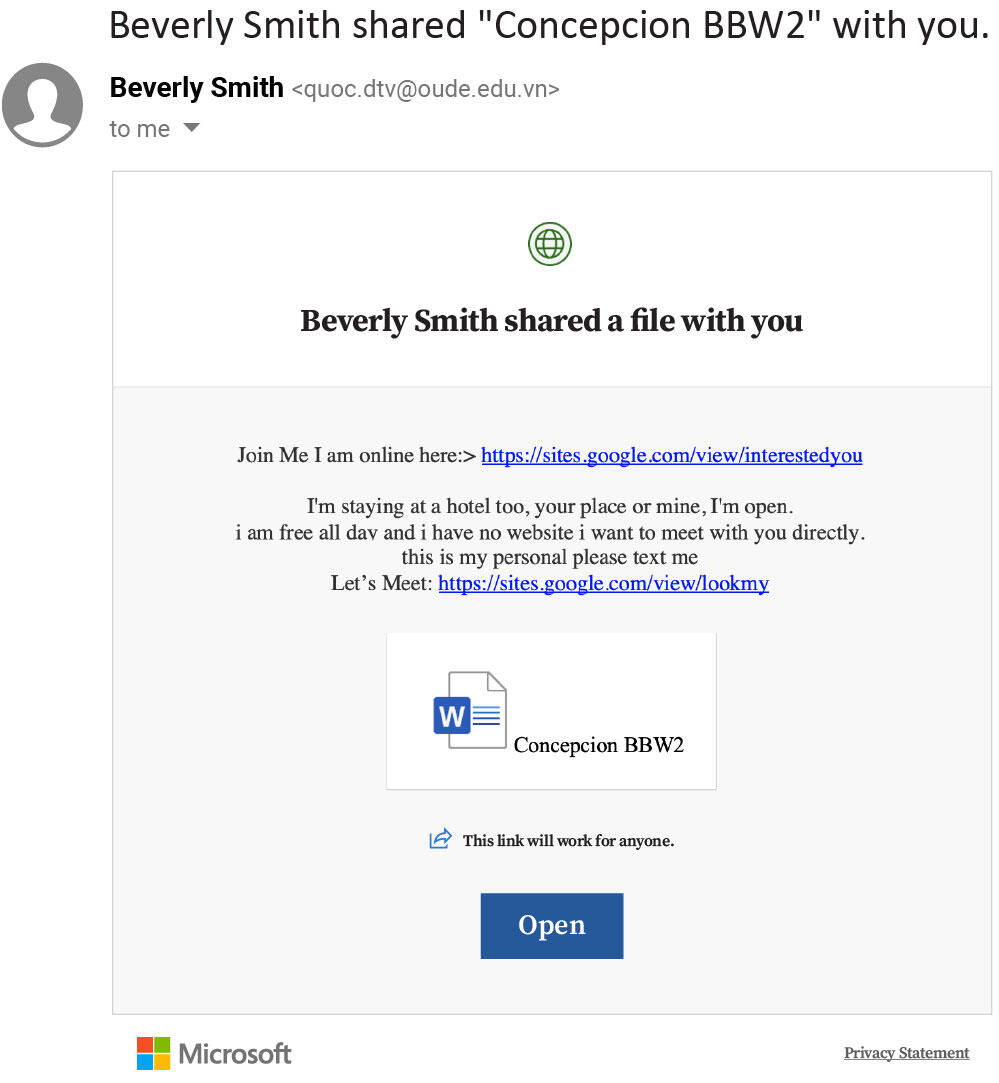
Image: GreatHorn
In the second one, the link in the email takes you to a site with X-rated photos. Here, you're asked to confirm your ZIP code to find potential hookups in your area. This site also seems to be designed to capture payment information, and any details collected will be used for blackmail and other malicious activities.
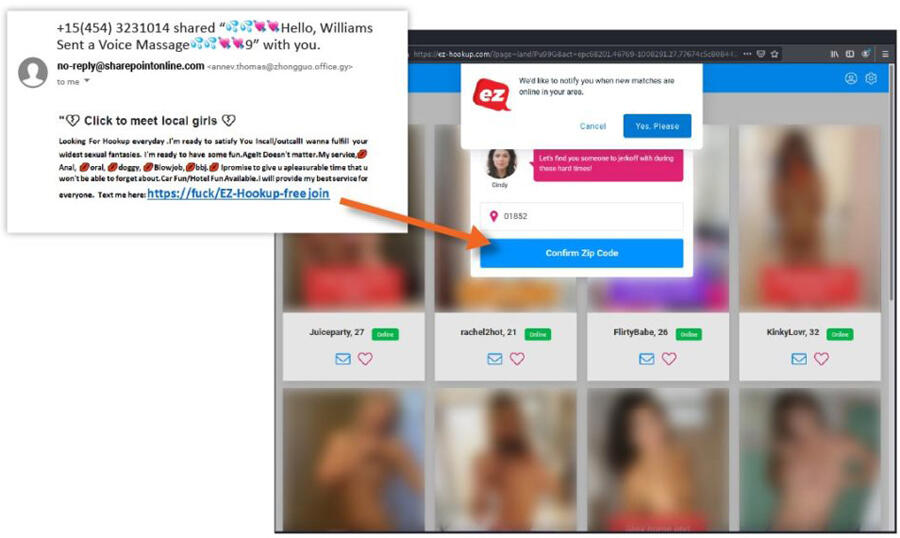
Image: GreatHorn
To protect your organization and users against these types of phishing emails, GreatHorn CEO and co-founder Kevin O'Brien offers the following tips:
Protect and engage your users. The old way of thinking centers on whether an email is good or bad. But today's email threats often fall into a gray area between the two sides. As such, a static rule-based defense that blocks "bad" emails will miss the gray spots. Instead, use more intelligent security tools that will highlight unusual aspects of a message. By pointing to suspicious content or elements in an email, these tools can reinforce whatever skepticism a user might have about a specific message and help them to learn to trust their instincts.
Back up security with training. No security awareness training program will ensure that your users engage with every email perfectly and make the right decision every time. But such training can change how your users interact with email, in general, to better protect your organization. You can also tailor your training efforts. For example, if a user receives more highly sophisticated email attacks, then add that tactic as another layer of training.
Get rid of "false positive" and "false negative" thinking. Instead, move to a mindset of "unusual" and "usual." Fashion your defenses around those factors, closely tied to NIST's cybersecurity framework or to MITRE's ATT&CK model.
Also see
"try" - Google News
June 02, 2021 at 11:12PM
https://ift.tt/2RdyL9M
How X-rated phishing attacks try to blackmail their victims - TechRepublic
"try" - Google News
https://ift.tt/3b52l6K
Shoes Man Tutorial
Pos News Update
Meme Update
Korean Entertainment News
Japan News Update
Bagikan Berita Ini














0 Response to "How X-rated phishing attacks try to blackmail their victims - TechRepublic"
Post a Comment