
Criminals behind a recent phishing scam had assembled all the important pieces. Malware that bypassed antivirus—check. An email template that got around Microsoft Office 365 Advanced Threat Protection—check. A supply of email accounts with strong reputations from which to send scam mails—check.
It was a recipe that allowed the scammers to steal more than 1,000 corporate employee credentials. There was just one problem: the scammers stashed their hard-won passwords on public servers where anyone—including search engines—could (and did) index them.
“Interestingly, due to a simple mistake in their attack chain, the attackers behind the phishing campaign exposed the credentials they had stolen to the public Internet, across dozens of drop-zone servers used by the attackers,” researchers from security firm Check Point wrote in a post published Thursday. “With a simple Google search, anyone could have found the password to one of the compromised, stolen email addresses: a gift to every opportunistic attacker.”
Check Point researchers found the haul as they investigated a phishing campaign that began in August. The scam arrived in emails that purported to come from Xerox or Xeros. The emails were sent by addresses that, prior to being hijacked, had high reputational scores that bypass many antispam and antiphishing defenses. Attached to the messages was a malicious HTML file that didn’t trigger any of the 60 most-used antimalware engines.
The email looked like this:
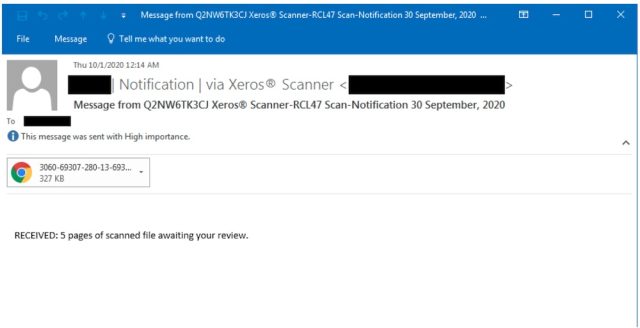
Once clicked, the HTML file displayed a document that looked like this:
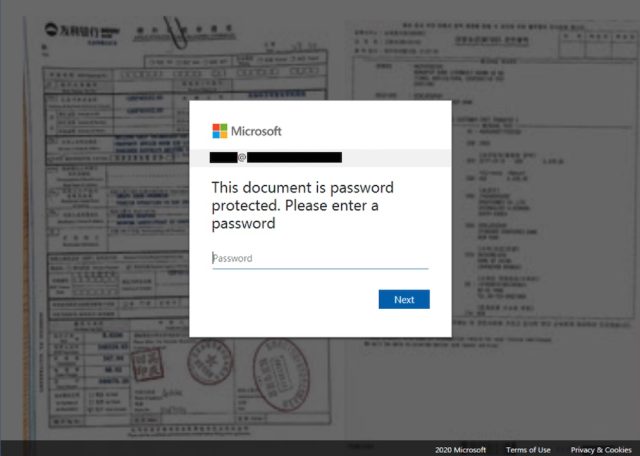
When recipients were fooled and logged into a fake account, the scammers stored the credentials on dozens of WordPress websites that had been compromised and turned into so-called drop-zones. The arrangement made sense since the compromised sites were likely to have a higher reputational score than would be the case for sites owned by the attackers.
The attackers, however, failed to designate the sites as off-limits to Google and other search engines. As a result, Web searches were able to locate the data and lead security researchers to the cache of compromised credentials.
“We found that once the users’ information was sent to the drop-zone servers, the data was saved in a publicly visible file that was indexable by Google,” Thursday’s post from Check Point read. “This allowed anyone access to the stolen email address credentials with a simple Google search.”
Based on the analysis of roughly 500 of the compromised credentials, Check Point was able to compile the following breakdown of the industries targeted.
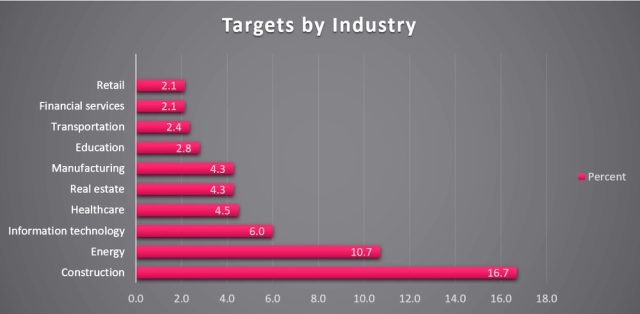
Simple Web searches show that some of the data stashed on the drop-zone servers remained searchable at the time this post was going live. Most of these passwords followed the same format, making it possible that the credentials didn’t belong to real-world accounts. Check Point’s discovery, however, is a reminder that, like so many other things on the Internet, stolen passwords are ripe for the picking.
"had" - Google News
January 22, 2021 at 04:00AM
https://ift.tt/3qAkqjM
Phishing scam had all the bells and whistles—except for one - Ars Technica
"had" - Google News
https://ift.tt/2KUBsq7
https://ift.tt/3c5pd6c
Bagikan Berita Ini














0 Response to "Phishing scam had all the bells and whistles—except for one - Ars Technica"
Post a Comment